It has managed to store photos and videos in the DNA of living cells, which could then be reproduced in a computer after being extracted. Now it wants to create a sun cream made with DNA that promises to be the best you’ve tried so far. Today, we are going to tell you how to get infected with malicious software inserted in DNA to a computer. It sounds like science fiction, right? When you think about what we have achieved so far, it does not seem so far-fetched.
Looking for faults in laboratory software
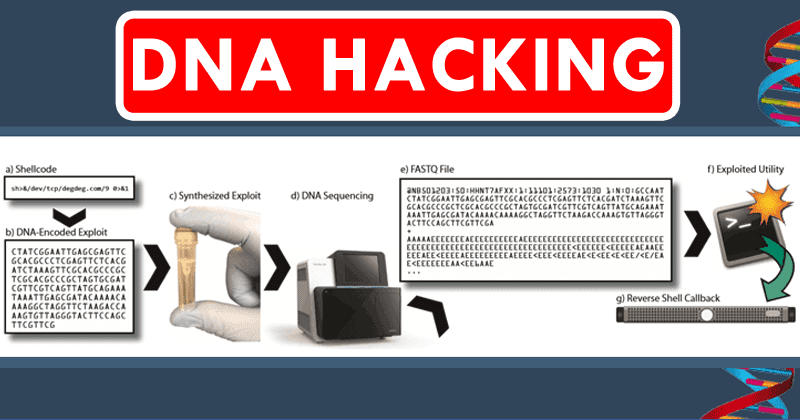
A multidisciplinary team at the University of Washington came to achieve this feat by researching the security of software used for transcription and DNA analysis in laboratories around the world. Due to the nature of the data being handled during these projects, it could be a big problem in the long run if no remedy is available. The team was able to demonstrate the weaknesses of the systems with typical viruses and remote access tools. This is how any threat would attack this system, but security experts wanted to stay current. “One of the most important things we’ve tried in the computer security community is to avoid a situation where we have to say, ‘Oh shit, opponents are knocking at our door and we’re not ready,’” said Professor Tadayoshi Kohno, whose History is replete with studies of vector attacks on electronic devices such as pacemakers. As we have seen, the molecular and electronic world is getting closer, so there are potential interactions that have never been contemplated. The main cause of this is CRISPR, which basically transforms the rows of DNA into data in binary code, that is, a potential virus.
Worthy of a mad scientist
“The conversion to ASCII of the cytokines, adenines, thymines, and guanines is performed in a fixed-size buffer that assumes a reasonable maximum reading length,” explained Karl Koscher when counting the process. This makes it a perfect target for a buffer overflow attack. After developing a way to include an executable code in the base sequence, they set out to start it. Although it can not be called a virus, it is close to being a “real” virus more than any other malicious code. “The exploit had 176 lines of code,” said Koscher. “The comprehension program altered each line into two bits, which packed together, became a 44-byte exploit when read.” This discovery opens the way to path infections that we had not contemplated. For example, you can create a person whose DNA is virtually deadly if you infect a computer with poor security. A future in which there are people who, in essence, are walking computer viruses is not pleasant. “It’s very difficult for a treated sample of malicious DNA to reach a sequencer, it’s a complicated challenge with many challenges.” Not that we are talking about a future biotechnological apocalypse, but the contemplation of it to avoid it is never too much. Kosher wants to study all these threats and viruses that can infect a lot of computers and other applications. This attack may be somewhat symbolic but may be another step closer to the union between the digital and biological revolution that is already happening. So, what do you think about this? Simply share your views and thoughts in the comment section below.
Δ